Summary: Strong cybersecurity is a fundamental element for a nation’s growth and prosperity in a global economy. A constant partnership between government, the private sector, and the community is becoming vital to developing a solid foundation within cyberspace. Such collaborations and initiatives from the state government are anticipated to deter cybercrime, thereby, necessitating larger business such as banks and telecom companies to build robust cybersecurity architect.
New business goals and innovative ways of working, such as Bring Your Own Device (BYOD), cloud computing, and other cross-channel collaboration are driving growth of various businesses. However, these activities expose an organization to cybersecurity threats. Cybercrime has become increasingly sophisticated, making the activity challenging to detect, deter, and counter. Thus, evolving landscape of threats and vulnerabilities has raised concerns of enterprises that continue to operate in cyberspace in private and public sectors. Moreover, need for secure cyberspace continues to proliferate with an increase in high profile data thefts and breaches. All these factors are anticipated to propel growth of the industry in the years to come.
Most Confirmed Cases Of Data Breaches Are Generally Executed By Organized Crime Groups Or State-affiliated Groups
Possibilities of various external and internal security threats were raised during the last decade. One of the top concerns to emerge was the lack of cybersecurity for countries with strong geopolitical position and nuclear capabilities. In the recent years, international organizations and governments of major countries have become more focused and increasingly aware of the urgency associated with the cybersecurity standpoint of a nation and its industries. The number of cybersecurity attacks reach a value of more than a thousand on a daily basis. With increasing sophistication and volume of cybercrime, these attacks are anticipated to spread across healthcare, financial institutions, and automotive sectors; that collect, process, and store a large amount of confidential data. Thus, technological advancements are expected to change the conduct of warfare in near future.
Cyber Security In Healthcare Sector
Growing penetration of Internet of Medical Things (IoMT) devices is predicted to exacerbate possibilities of cyber-attacks in healthcare. In addition, increasing investments to enhance healthcare technology can provide multiple entry points for cyber criminals to intrude. For instance, internet-based consulting with remote healthcare providers, multi-cloud Logging as a Service (LaaS) and Software as a Service (SaaS) environments, and connected medical devices; both inside hospitals and deployed with patients become vulnerable.
Following are the three major problems related to cybersecurity in healthcare sector and their possible solutions:
#1: Lack Of Investment
One of the most essential threats to hospital cybersecurity is lack of investment among small and mid-sized Health Delivery Organizations (HDO). Even some large scale healthcare entities lack in availability of appropriate solutions to evade cyberattacks.
Solution
In such scenarios, the very first step any healthcare organization should take is to work on asset inventory. They need to gather information about all the devices and information systems configured in their network and figure out how they all are interconnected to each other. Such information allows development of risk profile, security policy, and controls. Risk profile and security policy requires involvement of senior executives including Chief Technology Officer (CTO), Chief Revenue Office (CRO), Chief Financial Officer (CFO), and Chief Marketing Officer (CMO). After that the Chief Executive Officer (CEO) can approve arrangements necessary for risk-based investments, promotion of controls, and their enforcement.
#2: Lack Of Insurance
Second major vulnerability is lack of cybersecurity insurance. According to full-coverage cybersecurity insurance (FICO) for 2018, only 32% firms in U.S. have insurance that covers all risks associated with cyberspace. This survey is conducted by a consultancy firm Ovum for FICO through telephonic interviews with 500 senior executives from businesses in U.K., U.S., Brazil, Mexico, Canada, Germany, India, Finland, Norway, Sweden and South Africa.
Solution
It is mandatory for firms not covered under cybersecurity insurance to implement a stern system to prevent such security incidence. They need to make sure that the insurance covers all sorts of risks threatening all the systems in the network.
#3: Phishing Attack Resiliency Rate
Third problem is phishing attack resiliency rate. It measures the ratio between people who can report phish activity versus those who will fall victim to it. According to a recent survey by Cofense, healthcare resiliency rate for healthcare industry is expected to be 1.49 as compared to average resiliency score of 1.79 for other industries. This data is based on phishing simulations that Cofense utilized to test employees at customer organizations. Top five phishing scenarios that healthcare workers most frequently clicked on are manager evaluation, requested invoice, package delivery, Halloween ecard alert, and beneficiary change.
According to a recent Data Breach Investigations Report (DBIR), phishing and financial pretexting represented 93% of all breaches. Email is estimated to be main entry point to execute such activities. Attackers are also using phishing to deploy ransomware, which can account for 85% of malware in healthcare sector. In such phishing campaigns, attackers can pose as legitimate person or entity in an email to get target to provide sensitive information such as credentials. In addition, they can also ask targets to click on some link that can result in ransomware being downloaded on victim’s machine.
Solution
To combat phishing, organizations can train their employees on how to identify and ignore any phishing emails. In addition, they can also deploy appropriate technology to reduce possibilities of such attacks.
Cyber Security In Financial Sector
Another sector likely to be attacked by cybercriminals is the financial sector. It is the large amount of sensitive data available with these financial institutions, gaining traction among cyber attackers. In past decade, there had been numerous cyber-attacks reported by various financial institutes situated worldwide.
Following are the details for couple of major cyber-attacks:
#1: 143m Americans’ Social Security Numbers Exposed In Equifax Hack
Equifax is one of the largest credit rating firms in United States. It was attacked by cyber criminals in 2017 to steal sensitive user data. According to the company’s statement released immediately after the incident, hackers had been attacking a vulnerability on its website to access specific files containing sensitive data. That data included social security numbers, home addresses, birth dates, and driving license information. Around 143 million Americans were affected by this data breach. According to the company, 209000 credit card numbers were accessed by hackers, which included residents of Canada and U.K.
Solution
The moment Equifax came to know about= suspicious traffic on its online disputes portal, it immediately blocked that traffic. But, traffic was back again the very next day attributed to which company entirely took down the disputes app. After that, they hired Mandiant to conduct investigation and figure out the possible solution. To prevent such incidents, healthcare organizations can use programs like Flexera’s FlexNet Code Insight. They provide complete Bill of Materials (BOM) for open source and third party components in your code. In addition, they can even alert during Open-Source Security (OSS) vulnerabilities.
#2: Seven Of Biggest Banks In U.K. Attacked In 2017
Seven of biggest banks in U.K. including the Royal Bank of Scotland, Santander, and Tesco Bank were attacked by cyber criminals in 2017. All these banks were instructed to shut down their entire system. This attack was executed from a website called Webstresser.org by launching Distributed Denial of Service (DDOS) attacks. These attacks could flood and disable computer systems with high volume of internet traffic.
Solution
Following an investigation led by U.K.’s National Crime Agency (NCA) and Dutch national police, the website was immediately taken down. Servers on which this website was running were seized in Netherlands, Germany, and U.S. In addition, suspected members of group behind this attack were arrested in Scotland, Serbia, and Canada. After the arrest of masterminds, even the users of this website are likely to face prosecution and civil liability for caused damage.
Cyber Security In Automotive Sector
Automotive is the third major sector being targeted by cyber criminals. Growing number of capabilities offered by connected computer systems are likely to enable wide range of services and features. However, along with these advanced features and services comes the threat of malicious attacks, where systems controlled can be vehicles or vehicles related systems. In such scenarios, the consequences of any sort of failure can be worse.
#1: Tesla Model X Hacked By A Chinese Group
Recently, a group of Chinese researchers hacked Tesla Model X. This was a complex hack, according to which the group was able to get complete control of the vehicle. They could apply brakes, open and close doors or trunk, blink lights, and even play music through Wi-Fi or cellular connection.
Solution
When Tesla officials got to know about this hack, they acted immediately and fixed the problem within two weeks.
#2: Jeep Cherokee, Ford Escape, And Toyota Prius Hacked
Two engineers doing consulting work for Pentagon’s defense advanced research projects recently hacked Jeep Cherokee by Fiat Chrysler, Ford Escape and Toyota Prius to compromise their safety and sync systems and gain access. Based on this hack, these engineers could control brakes, cruise control, parking assist, steering, and even remote keyless entry system. Moreover, according to recent research on models of some specific cars designed by these engineers, most of them had security vulnerabilities.
Solution
After knowing about some serious software vulnerabilities, Fiat Chrysler Automobiles immediately took action and recalled 1.4 million of its vehicles.
Innovations In Cyber Security
Homographic encryption is an impressive technology that can allow encryption of data-in-use and can offer tremendous potential to lock down most valuable medical information. It can secure sensitive medical records and personally identifiable information (PII), often in target of cyber criminals.
In a recent development, Audi announced the upcoming launch of advanced Artificial Intelligence (AI) cars in collaboration with NVIDIA. The first phase of this new collaboration is expected to focus on NVIDIA DRIVE PX. It is an AI platform for self-driving cars, which is likely to use trained AI neural networks to understand surrounding environments and to determine safe path.
Moreover, Tesla recently added Personal Identification Number (PIN) option to its models for advanced security purposes. Aimed at combating theft of cars through hacking, this new option will not allow anyone to drive the car until correct PIN is entered on infotainment screen.
Source: Grand View Research
Factors Driving Adoption Of Cybersecurity Solutions
#1 Growing Stringency Of Government And Compliance Regulations
Increasing stringency of government regulations regarding data security and privacy and compliance is propelling adoption of cyber security solutions on global scale. In February 2016, the President of United States announced implementation of the Cybersecurity National Action Plan (CNAP) to strengthen cyberspace. He also issued an executive order to create a commission for promoting national cybersecurity as a central feature of CNAP. The Cybersecurity Act of 2015 encourages and promotes private sector and the U.S. government to rapidly and responsibly exchange cyber threat information. The Cybersecurity Enhancement Act of 2014 aids creation of voluntary public-private partnerships to improve security and strengthen the cyber warfare research and development activities.
In July 2015, as a part of China’s National Security Initiative, the Standing Committee of the National’s People’s Congress released the cybersecurity law to boost adoption of effective and coordinated approaches aimed at safeguarding the cyberspace. Furthermore, in 2016, a major transformation occurred within the Australian military, as it incorporated a new cybersecurity unit into its defense strategy.
#2 Growth In Penetration Of Cloud-based Security Solutions
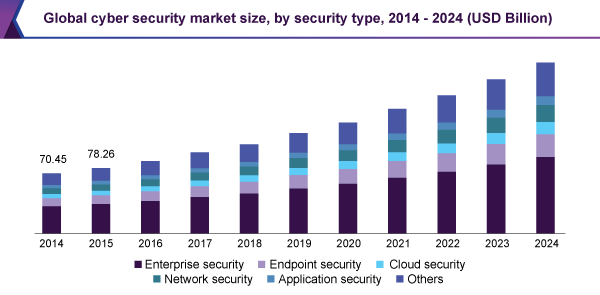
According to Grand View Research, the global cloud security market size was valued at USD 4.88 billion in 2016. It also expects the size of cybersecurity industry to surpass USD 200 billion in the next three to four years. The introduction of cloud storage has increased the threat of cybercrimes and data breaches across verticals such as defense, government, and homeland security, among others. These verticals prefer using cloud security solutions as the costs incurred in the implementation of on-premise solutions is high. Adoption of cloud-based security is expected to remain high in near future, owing to growing adoption of cloud storage systems and deterrence of cyber espionage.
The use of these security solutions is anticipated to increase the number of projects using cloud services. Government authorities prefer cloud platforms for data sharing as it leads to greater savings. Moreover, several commercial and government organizations are migrating to cloud storage, resulting in growth of security solutions for mitigating cyber threats and vulnerabilities.